SparkOnSoft campaign continues and mutates
Intro
Recently we on reported on SparkOnSoft which our Active Ransomware Prevention platform prevented in multiple customers’ environments worldwide.
Since then we’ve noticed that not only the campaign continues, it also mutates as new samples use another PDF application signed by a different certificate
Basic Information
The new payload is a PDF application called Proton PDF though the file name starts with ClearEdit and the file was signed with an Extended Validation certificate by Hawk Integrated Inc issued by Sectigo
Interestingly, the payload is a NSIS installer while SparkOnSoft samples, including new ones, still use InnoSetup to create the installers
The new payload is identified as part of the SparkOnSoft campaign according to VirusTotal (see IOCs below)
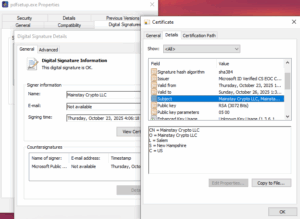
In addition, since our last post our prevention platform identified more samples which were still being downloaded from sparkonsoft[.]com and are still signed by Mainstay Crypto LLC issued by Microsoft

IOCs
- SHA2: 686d018c86c03165925ebd3773c622f182c93f54b98db9616bae86f5e8684e4c (Proton)
- SHA2: 91e4f66fb2af51fa3b2e0463c8c140e628d5d057cadde3f7d4d4bcb991289a38 (Spark)
- SHA2: 73dbd23bb38472c1a9a3b0fb6f3ed5c9c272204e01de4bd35fed6034bf3c463b (Spark)
- SHA2: 4fa777e1392037fde13b8e93b7d69427926fca5000b816f562e829c9246f46c9 (Spark)
- Compromising websites: hxxps://pdfproton[.]com and hxxps://[*.]getpdfproton[.]com
- Compromised AWS S3: hxxps://internalcomponentspdf[.]s3.us-east-1.amazonaws.com (Spark)
Don’t Miss a Thing
Sign up today and we’ll send an email when new posts come out.
We collect and use this information in accordance with our privacy policy.